CONFIGURATION
ET UTILISATION DE SNORT
& SNORT ALERT VERIFICATION
I) Utilisation basique
de SNORT
Nous utilisons SNORT de 3 façons
différentes :
- Sniffer
- Packet logger
- IDS
L’ utilisation en mode Sniffer et Packet logger est assez simple,
une seule ligne de commande suffit pour le lancer.
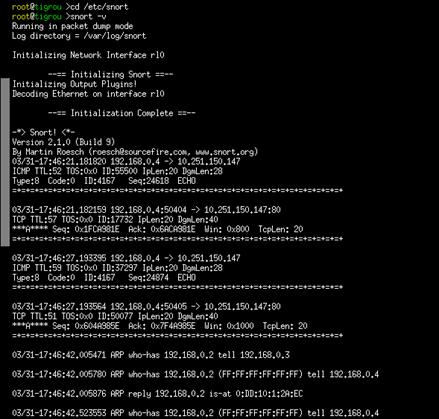
1. Sniffer
Un sniffeur est un programme lancé
permettant de capter les datagrammes qui passent sur un réseau, et de les
rendre lisible pour l'être humain.
On peut ainsi savoir ce qu'il se passe sur le réseau, et ainsi détecter les
sources de problèmes.
Pour utiliser SNORT en mode verbose, et
afficher les entêtes TCP/IP :
# snort –v
Pour afficher les IP et les en-têtes TCP/UDP/ICMP :
# snort –vde
2. Packet logger
En mode packet logger, il n’ y a plus de sortie en console, mais
dans un fichier de logs .
Le répertoire de logs par défaut est /var/log/snort.
Pour loguer l’ activité
dans un répertoire donne :
# snort -de -l mylog_dir
Ces logs sont en mode texte.
Il est possible d’enregistrer les logs en mode binaire, c’est plus rapide
et exploitable par la suite.
# snort -l /var/log/snort
–b
II) Utilisation en mode
IDS
Un IDS est un système combinant logiciel et matériel, qui permet de
détecter en temps réel les tentatives d'intrusion sur un réseau interne ou sur
un seul ordinateur hôte, de neutraliser ces attaques réseaux ou systèmes et
d'assurer ainsi la sécurité du réseau d'entreprise.
Configuration
Le fonctionnement de SNORT en mode IDS repose sur :
- Un fichier de configuration
- Des fichiers de règles
- Un fichier de classification des alertes
Les règles servent à reconnaître et à déclencher une action lorsque SNORT
voit passer un paquet répondant à certains critères.
Par exemple, des paquets sont caractéristiques de recherche de failles de
sécurité, ou de scans.
Nous avons configure SNORT ainsi
Détail du fichier de
configuration de SNORT (snort.conf)
Nous avons défini le réseau à surveiller :
var HOME_NET
192.168.0.0/24
Le serveur DNS :
var
$DNS_SERVERS [10.42.6.6/32]
Ensuite, nous avons défini le
répertoire ou se trouvent les règles :
var RULE_PATH /etc/snort/rules
Puis, les preprocesseurs, charges de traiter les paquets
preprocessor portscan: $HOME_NET 4 3 /var/log/snort/portscan.log
preprocessor http_decode: 80 unicode iis_alt_unicode double_encode iis_flip_slash full_whitespace
Nous avons mis en place une base de données MySQL
pour recenser les alertes. Ensuite, nous utilisons Apache pour voir ces logs.
var output database: log, mysql, user=snort
password=snort
dbname=snort host=localhost;
Règles utilisées :
include $RULE_PATH/bad-traffic.rules
include $RULE_PATH/exploit.rules
include $RULE_PATH/scan.rules
include $RULE_PATH/finger.rules
include $RULE_PATH/ftp.rules
include $RULE_PATH/telnet.rules
include $RULE_PATH/rpc.rules
include $RULE_PATH/rservices.rules
include $RULE_PATH/dos.rules
include $RULE_PATH/ddos.rules
include $RULE_PATH/dns.rules
include $RULE_PATH/tftp.rules
include $RULE_PATH/web-cgi.rules
include $RULE_PATH/web-coldfusion.rules
include $RULE_PATH/web-iis.rules
include $RULE_PATH/web-frontpage.rules
include $RULE_PATH/web-misc.rules
include $RULE_PATH/web-client.rules
include $RULE_PATH/web-php.rules
include $RULE_PATH/sql.rules
include $RULE_PATH/x11.rules
include $RULE_PATH/icmp.rules
include $RULE_PATH/netbios.rules
include $RULE_PATH/misc.rules
include $RULE_PATH/attack-responses.rules
include $RULE_PATH/oracle.rules
include $RULE_PATH/mysql.rules
include $RULE_PATH/snmp.rules
include $RULE_PATH/smtp.rules
include $RULE_PATH/imap.rules
include $RULE_PATH/pop3.rules
include $RULE_PATH/nntp.rules
include $RULE_PATH/other-ids.rules
include $RULE_PATH/web-attacks.rules
include $RULE_PATH/backdoor.rules
include $RULE_PATH/shellcode.rules
include $RULE_PATH/policy.rules
include $RULE_PATH/porn.rules
include $RULE_PATH/info.rules
include $RULE_PATH/icmp-info.rules
include $RULE_PATH/virus.rules
include $RULE_PATH/chat.rules
include $RULE_PATH/multimedia.rules
include $RULE_PATH/p2p.rules
include $RULE_PATH/experimental.rules
include $RULE_PATH/local.rules
Lancement de snort, en full logging, dæmon, sur
l’ interface vr0, en logguant dans
/etc/snort/snort.conf, et en utilisant un fichier de configuration choisi
# snort -A full
-d -D -i vr0 -l /var/log/snort
-c /etc/snort/snort.conf
SNORT Alert Verification
Integre un module de verification
des alertes de SNORT.
Lancement de snort (en mode alert) : Marque les alertes établies
comme faux positifs
# snort -A full
-d -D -i vr0 -l /var/log/snort
-c /etc/snort/snort.conf –a mark
Lancement de snort (en mode alert) : Efface les alertes établies
comme faux positifs
# snort -A full
-d -D -i vr0 -l /var/log/snort
-c /etc/snort/snort.conf –a suppress
Strategie de placement des IDS sur le reseau :
Les IDS sont places derrière le routeur, et nous
avons mis en place une duplication des paquets au niveau du routeur, de telle
sorte que les paquets arrivant de l’ extérieur (attaque) vers les serveurs sont
clonés et envoyés aux IDS